DevOps automation for Trend Micro in AWS Marketplace using AWS Service Catalog and AWS Systems Manager Distributor | AWS Marketplace
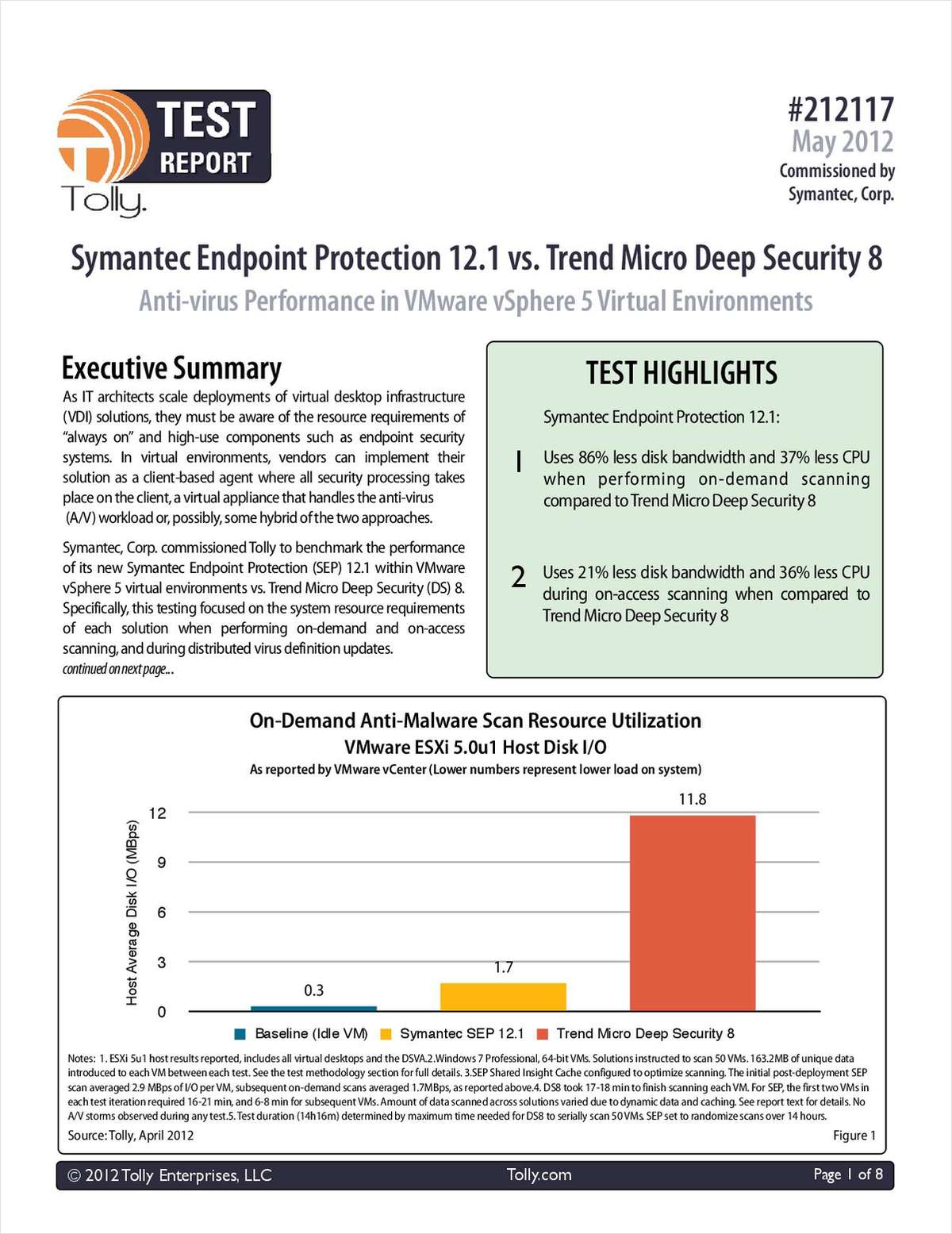
Tolly Report: Symantec Endpoint Protection 12.1 vs. Trend Micro Deep Security 8 - Paperpicks Leading Content Syndication and Distribution Platform